Pattern Matching Hyphen-Minus Sign in Bash
I was trying to use the sed command to perform some changes to a text and stepped into an interesting “problem”; pattern matching the minus-hyphen (-) symbol.
Assume we have the following text:
something SoMeThiNg some-thing soMe_thing
and we want to match all the different versions of the word with one expression (one by one).
My initial idea was to use this regular expression:
's/[a-zA-Z\-\_]*/matched/' |
Naturally, I tried to escape the – sign. As you can see from the output, this doesn’t work:
$ sed 's/[a-zA-Z\-\_]*/matched/' test matched matched matched-thing matched |
The minus sign is not matched, because of its special meaning (setting ranges). In order to make the expression work, you need to move the “-” either in the beginning or in the end of the expression:
$ sed 's/[a-zA-Z\_-]*/matched/' test matched matched matched matched $ sed 's/[-a-zA-Z\_]*/matched/' test matched matched matched matched |
and leave it un-escaped!
Microsoft Translator Bot (TBot)
Have you ever heard of Microsoft’s Translator Bot, known as TBot? It is a bot that you can add as a contact in your Windows Live (msn) account and can be used for automated translation. You just need to add mtbot@hotmail.com as a friend. Read more here.
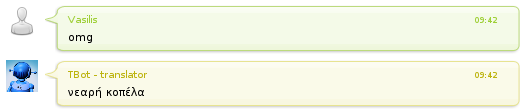
I post this because I was playing with TBot and I stepped into a very nice English to Greek Translation:
Everyone knows what “omg” stands for, right? Oh My God..
Well, “νεαρή κοπέλα” is “young girl” in Greek :-O.. Even TBot knows that:

Top 25 Most Dangerous Software Errors
The 2011 CWE/SANS Top 25 Most Dangerous Software Errors is a list of the most widespread and critical errors that can lead to serious vulnerabilities in software. They are often easy to find, and easy to exploit. They are dangerous because they will frequently allow attackers to completely take over the software, steal data, or prevent the software from working at all.
The Top 25 list is a tool for education and awareness to help programmers to prevent the kinds of vulnerabilities that plague the software industry, by identifying and avoiding all-too-common mistakes that occur before software is even shipped. Software customers can use the same list to help them to ask for more secure software. Researchers in software security can use the Top 25 to focus on a narrow but important subset of all known security weaknesses. Finally, software managers and CIOs can use the Top 25 list as a measuring stick of progress in their efforts to secure their software.
Find the list here.
Revover Encrypted Home Directory – Ubuntu 11.04 live
I am having some problems with my hard-drive, so I was trying to backup my data the reside on my encrypted (the default Ubuntu encryption) home directory.
Ubuntu 11.04 offers a command (ecryptfs-recover-private) that help you perform this operation easily. Simply follow the steps:
- Boot Ubuntu 11.04 with a live-cd or usb.
- Mount the partition that includes the encrypted directory. You can easily do this by selecting
Places -> PartitionName. - Open a terminal (
Applications -> Accessories -> Terminal). - Run
sudo ecryptfs-recover-private
You will be prompted to enter the password that corresponds to the user of this partition. After this, the partition should be mounted at a folder indicated by the output of the command.
Introduction to Erlang : Shared Memory Example
Shared Memory
This post will be about building step by step a shared memory abstraction in Erlang. As you should all know, variables in Erlang are immutable; once a variable is bound to a value, this value cannot change. Thus in order to implement a mutable variable/object we need to represent it with a recursive process responsible for keeping the current value and providing the interface for using the object (read and write operations for example).
So, in order to implement a memory abstraction we have to use the aforementioned approach. We can either create a single process to be responsible for keeping the whole address space as a simple list, or create one process for each allocation operation. We will follow the second approach because it is more interesting and protects the memory process from becoming the bottleneck.
Let’s start!
The Messaging Interface
The interface of the memory system is quite simple. We just need the following operations:
start: for starting the memory systemstop: for stopping the memory systemalloc: for allocating memoryfree: for freeing memoryread: for reading the value of a memory addresswrite: for writing to a memory address
From the above, the four first operations will be handled by the memory system, while the two last by each memory address (process) that they refer to. We will create two modules:
mem: the memory systemmemif: the memory interface
and one file called “common” with the parameters of the system.
-define(MEMREGNAME, mem). -define(MAXSIZE, 100). |
This file will be include in both other modules (-include("common") directive).
Read the rest of this entry »
Introduction to Erlang : Concurrency (Processes)
Concurrency
Concurrency is defined as “the temporal property of two things happening at the same time” (according to WordNet). In Computer Science, the definition is “concurrency is a property of systems in which several computations are executing simultaneously, and potentially interacting with each other. The computations may be executing on multiple cores in the same chip, preemptively time-shared threads on the same processor, or executed on physically separated processors.” (according to Wikipedia).
In practise, if two, or more, tasks are concurrent, then they can run in parallel. This implies that there are no data dependencies among them. For example, the following tasks
- unlock the car (the car was locked)
- start the engine of the car (the engine was off)
- drive the car
are non-concurrent since they have dependencies. One cannot start the engine of the car without first entering the car and she cannot drive it without first starting the engine. These tasks have to be executed sequentially (with a predefined order) no matter if more than one person (processing unit) help. On the other hand
- doing the laundry
- washing the dishes
- go for shopping
can be potentially run in parallel. For example, three different family members can handle one task each. Moreover, if only one person has to do all the tasks, she can decide to perform them in any order she decides since there are no dependencies among them.
Read the rest of this entry »